AWS re:Invent re:Actions — Controlling risk is important, but confusing
Datica Alumni — Former Chief Marketing Officer
Last week the Datica team visited Las Vegas for the annual AWS re:Invent conference. As always, the event did not disappoint. AWS knows how to put on a show, getting grander every year. Here are a few observations from Datica’s point of view.
The MBAs got a hold of the cloud
In last year’s review I made a comment that has since been a story I tell when discussing the state of the cloud. It went something like this:
In 2014, 2015, and 2016, the cloud was still portrayed as a toy for developers. Most vendors on the expo floor focused on developer empowerment, and most tools were about building things. The sky was the limit.
Then in 2017, it’s like the MBAs got a hold of the cloud. It was stark how many new vendors flooded the expo, peddling tools to help control costs and security concerns.
If we thought 2017 was about shifting away from being a toy, 2018 cemented that the future of the cloud is about controlling the cloud.
The overwhelming majority of vendors present were focused on tools to manage security, compliance, cost, and governance. In short, risk.
This is actually a good thing, much to the likely disappointment of engineers: Now that the cloud is considered a strategic part of the “business” it must be managed as if it’s part of the business. Consequently, more cloud adoption is definitely on the horizon.

It is hard for buyers to know what to buy
While the overwhelming majority of tools are now focused on controlling the cloud, which is a good thing, the negative side is that the space around how to control your cloud is very confusing.
Many tools tout “guardrails” and “policy-driven development”, among many other terms of art. In the end, no matter how you slice it, there are too many companies saying too many different things while doing too similar of jobs. The recipe is buyer confusion, which isn’t going to help with cloud adoption. An anecdote to underscore the point: across from the Datica booth was ZoHo — you know, the old-school CRM company — featuring a security monitoring service for AWS services; similarly, behind the Datica booth was CapitalOne — you know, the credit card company — who offered an undifferentiated security automation platform.
By our count, there were over 35 different companies with a booth (plus consultancies like Accenture, et al) featuring some sort of security or governance tool. Dizzying.
This point is a good reminder to explain why Datica is different. We are very conscious of the fact that the security and compliance landscape has evolved considerably the last few years, which is why we are laser-focused on solving the specific problem Datica is best positioned to solve: managing healthcare-specific compliance on AWS, Azure, and GCP.
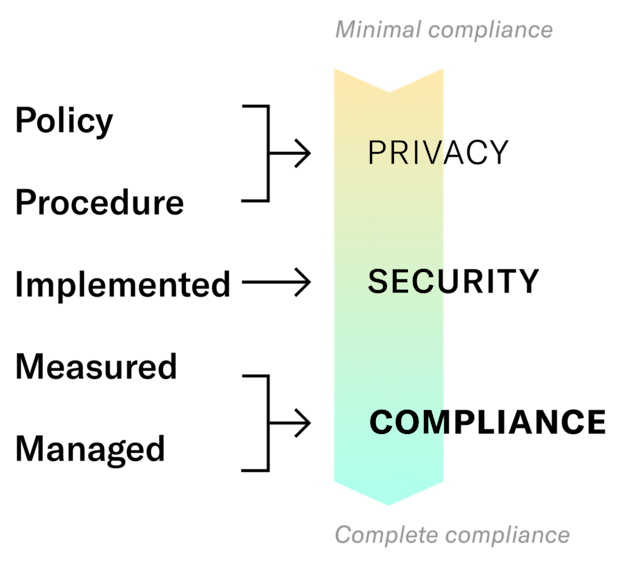
We uniquely solve this problem because we are focused on the business problem of compliance, and not the technical or functional a single developer faces. The best way to explain is through the concept of the maturity model.
Visualizing the business problems of compliance
What is a Control?
Example: "Users shall only be provided with access to internal and external network services that they have been specifically authorized to use. Authentication and authorization mechanisms shall be applied for users and equipment."
Each piece of technology needs to go through a similar process.
This is an example Capability Maturity Model that some frameworks use to understand the maturity of controls.
Over the last five years, Datica has been the expert at understanding the exact policies and procedures required to turn HIPAA-eligible services on the public cloud into architectures that can pass a HITRUST CSF assessment. The focus on policies and procedures (levels 1 and 2) then allows our customers to implement (level 3) the appropriate security controls with context. When complete, customers can then be assured that measuring and managing (levels 4 and 5) lead to the compliance verification required to pass audits. That’s what matters.
In contrast, the plethora of security tools flooding the space are just that—security tools, a.k.a level 3 implementation tools. They are functional pieces of software that allow developers to do security for the sake of security. Which, to be clear, is not a bad thing—all security is good in practice. However, within a healthcare context, organizations must be able to document and attest to security implementations that map all the way back to regulatory rules. Privacy → Security → Compliance. The challenge of unaware security still exists with all other security tools, but not with Datica.
AWS Comprehend is interesting
AWS launched a new service called Comprehend. It’s a natural language processor (NLP) tool for unstructured data sitting within EHRs. It was developed by a talented team led by Arun Ravi.
Compliance is an area that still needs to be managed. An important disclaimer about compliance by the product:
“AWS Comprehend does not meet the requirements for de-identification of protected health information under HIPAA. You are responsible for reviewing any output provided by Amazon Comprehend Medical to ensure it meets your needs.”
We are interested to see the use cases develop over the next few years. If you are working on a project and are interested in this service, but are unsure about the compliance requirements, feel free to email us.
It should be said, too, that getting the data is a critical requirement to use Comprehend. Datica’s EHR integration service CMI is still the best service available. When combined with one of our compliance management tools, Comprehend is positioned to make an influential impact on clinical care. We’re excited to see what our customers will do with it.
Outposts is the actual interesting part about healthcare and the cloud in 2019
Lastly, the announcement about the partnership with VMware to install AWS services and APIs on-prem via the new AWS service called Outposts was very interesting in a healthcare context.
This announcement is an interesting concession by AWS. With it, they are acknowledging that not only will it take time (decades) for certain cloud workloads to migrate from old data centers to the public cloud, but that some workloads will never migrate.
Azure has been operating under this point of view for a while with Azure Stack, and this appears to be AWS’s answer. Azure has had success in this area; time will tell if AWS can match it.
Why this matters in healthcare should be pretty obvious: only a tiny fraction of healthcare workloads have actually made it to the public cloud so far. The vast majority still sit with legacy systems, buried in a basement or at a co-location facility.
- Compliance is still a confusing concern for many healthcare organizations, with a majority still preferring to control even the data center in order to pass audits.
- Update cycles are the longest of any industry. Many systems are at least 10 years old! It takes years for patches to happen.
- “If it’s not broke, don’t fix it.” What does that phrase mean within a healthcare context? Well, “break” doesn’t mean using an outdated database… “break” means, “Did people die?” Long story short: changing software that has proven to not kill people, to unknown software that could break and kill people, is a very different calculus than non-healthcare developers realize.
- EHRs will never be on the public cloud, generally speaking. Athena is making the biggest push and could do it, with Cerner an interesting observer. But, over the next decade, EHRs will never be on the cloud. Therefore with the central patient data repository sticking on-prem, why start to split your data to the public cloud?
These are among many other developments. The bottom line is that AWS Outposts, along with Azure Stack, are the true trojan horses to try to bridge healthcare data from old data centers to the public cloud.
